“How secure is your network?”
We’ve had the question asked a few times, so we figured it was appropriate to write a blog post about it. Without going into alot of technical details, I will highlight standard security practices and how you can implement them in your own home network.
Segregating our network –
We have broken our network into different segments either physically or through virtual means like VLANs. This allows us to contain any security breaches (if/when they occur) to a single zone/segment of our network. We can also apply different security controls and monitoring to each zone.
How might you segregate your network? There’s many different ways you could protect your home network with segregation. For example, maybe you put your guest wifi on a different VLAN and SSID so if one of your guests arrives with a hacked device, they won’t infect your network. Or perhaps you want to throw your IoT devices or smart devices into a different virtual network. Or maybe your security cameras, you want to be on a physically different network with tighter security measures. There’s many ways you can use this method to improve the security of your network.
Lock down the network –
This one is pretty broad. So for starters, network gear is physically secured with layers of physical security – locked facility, locked cabinets, security cameras, etc. Then there’s digital security. All devices have different secure passwords. Multi-factor Authentication (MFA) is deployed wherever possible.
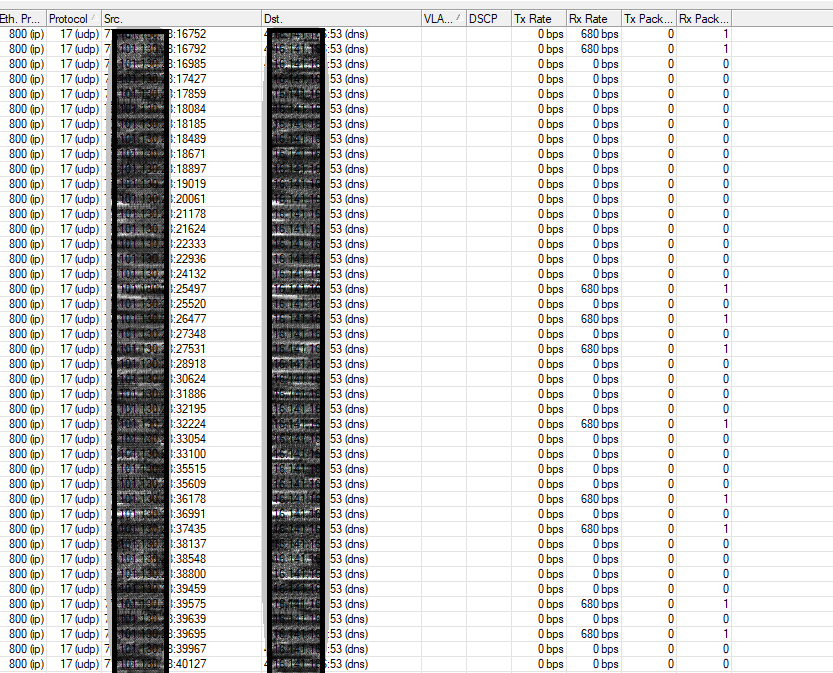
From a firewall standpoint, by default everything is disabled and blocked. We only open what’s necessary to conduct business. This helps prevent things like DDoS attacks, DNS Amplification attacks, and so on. Take the screenshot below for example – this is just one filter – a DNS Amplification that would be bad for the network. We are blocking over 1000+ outside DNS requests per second (at the time of this writing).
How can you implement a lockdown on your network? For one, physical security isn’t a bad idea. Don’t leave your router and switches in plain sight. If you have a device that has Wifi built it, those usually don’t fare well in a cabinet. Consider a standalone Wifi Access Point. There are many ceiling mount units that look really nice, provide better coverage throughout your home, and add to that physical layer of security.
Make sure your firewall is enabled on your router. Alot of modern routers have tons of features on them. Only enable the ones that you are using. Otherwise, you are opening potential holes into your network. Think of it this way, a lock on your front door does little good if you have several windows in the house open.
Use strong passwords. I could write an entire blog post about just this. Make sure you aren’t using the default passwords on your router, your Wifi’s SSID, etc. We talked earlier about guest wifi – so I’ll talk about that again for a minute. Your normal wifi should have a cryptic password. Make it so long that your eyes cross when you go to type it. Then maybe you have your guest wifi password a little easier. It should still be secure, but can be a phrase that’s easy to remember. While you are at it, if you have the ability to throttle your guest wifi – do it. That way if someone, somehow got your guest wifi password, they aren’t able to consume all of your available internet connection.
Using Network Address Translation (NAT) –
This translates private IP addresses of our network to the public IPs for external communication to the internet. IPv4 has long been exhausted, so conserving this resource is important. That’s where NAT comes in play. By default, we don’t hand out public IPs to customers. This helps conserve our IPv4 allotment, but also provides a level of privacy and security to your networks. Instead of a public IP being exposed directly to your router, you get an internal IP. If you want a public IP, this can still be accomplished for an added cost. Contact us for details.
It has long been said that NAT causes issues with Gaming and VOIP services. However, this is becoming less a problem as providers have seen the need for NAT more than ever with IPv4 running out.
How do you use NAT on your network? Most consumer routers have NAT enabled automatically. This is what makes the 192.168.0.x IPs on your network and allows devices to still talk to the internet.
Monitoring everything –
No matter how much and what you implement for security – monitoring is critical. Looking for new holes, new exploits, and disabling or blocking what’s not needed. Monitoring also allows us to know when there’s abnormal traffic that would indicate a potential issue or if there’s an outage.
There’s simply too much to cover regarding network security, and how we have secured our network. There are whole organizations (government and otherwise) that develop metrics and standards for data handling and security. I’ve touched on just a few of the ones that we’ve used and ways you can implement them in your network. If you are super serious about your network security, feel free to reach out and one of our team members can put you in touch with a consultant to implement the best practices for your network.
